Overview:
What is DHCP?
-
Dynamic Host Configuration Protocol (DHCP) is a network protocol that automatically assigns IP addresses and other configurations to devices when they connect to a network. DHCP can also assign Domain Name System (DNS) addresses, subnet masks, and default gateways.
What is DHCPv6 Poisoning
-
DHCPv6 DNS poisoning allows an attacker to control the DNS server address of a victim, effectively poisoning the service so that the victim will communicate with an attacker-controlled system. In this type of attack, the attacker spoofs a DHCP server response, including a DNS configuration.
-
Risks of DHCPv6 Poisoning:
-
SIEMs, IPS/IDS, Firewalls, and many network monitoring tools have much better support for IPv4 than IPv6. This means, some older firewalls may not have any visibility or blocking capabilities for IPv6.
- IPv6 being a newer protocol has many vulnerabilities in which can be exploited by an attacker.
- Fragmentation attacks can be used in IPv6 to bypass firewalls or IDS systems, as some systems struggle to handle IPv6 fragmentation properly.
- Privacy concerns with IPv6 addressing. IPv6 addresses are often based on a device’s MAC address (via EUI-64), which can expose the device’s unique hardware identifier, allowing for device tracking across networks.
- IPsec is mandated for IPv6, but it is often not fully implemented, leaving traffic exposed.
- Transition mechanisms such as 6to4, Teredo, and ISATAP are used to allow IPv6 traffic to pass through IPv4 networks. These tunneling protocols can create security blind spots, as the encapsulated IPv6 traffic might bypass security devices that only inspect IPv4 traffic. Attackers can exploit these mechanisms to circumvent firewalls, gain unauthorized access, or bypass network segmentation controls.
-
Potential implementation impacts to watch out for:
-
There are no known issues with this DHCP mitigation technique at this time. Preferring IPv4 over IPv6 still allows IPv6 to function as needed, but also mitigates most of the vulnerabilities associated with this risk.
Technical Deployment:
Creating a GPO for DHCPv6 Poisoning remediation:
-
Configure clients to prefer IPv4 over IPv6: This can be accomplished with a registry update. Setting the value of HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip6\\Parameters\\DisabledComponents to decimal 32 will configure Windows to prefer IPv4 over IPv6.
-
Create disableIPv6.ps1 with the following contents.
# Create registry key if it doesn't exist
$regKey = "HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters"
if (!(Test-Path -Path $regKey)) {
New-Item -Path $regKey -Force | Out-Null
}
# Set the registry value
Set-ItemProperty -Path $regKey -Name "DisabledComponents" -Value 0x20 -Type DWord
-
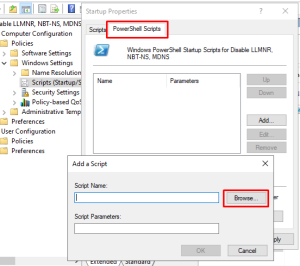
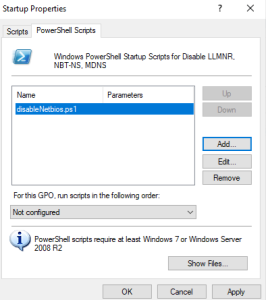
Computer Configuration -> Policies -> Windows Settings -> Scripts -> Startup (Properties) -> PowerShell Scripts -> Add
-
-
Startup scripts need to be placed in locations that are accessible to clients. For most environments, you’ll probably be alright by placing it in the SYSVOL volume together with the GPO itself.
-
Click the Browse button and paste the startup script into the location that explorer opens in and accept all the prompts (Except use the appropriately named version to this guide)
-