Overview:
What is LLMNR + mDNS (Multicast DNS) + NBNS (NetBios Name Service, or NetBIOS over TCP/IP)
- LLMNR was (is) a protocol used that allowed name resolution without the requirement of a DNS server. It was (is) able to provide a hostname-to-IP based off a multicast packet sent across the network asking all listening Network-Interfaces to reply if they are authoritatively known as the hostname in the query. It does this by sending a network packet to port UDP 5355 to the multicast network address (all layer 2).
- Risks of LLMNR being enabled:
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept LLMNR requests and respond with false information, redirecting traffic to malicious servers. This can lead to credential theft if users attempt to connect to these rogue servers.
- Name Resolution Poisoning: An attacker can spoof legitimate hostname resolutions by responding to LLMNR queries faster than the legitimate server, leading to potential data interception or redirection of network traffic.
- Credential Theft: When LLMNR is exploited in combination with tools like Responder, attackers can capture NTLMv2 hashes from victims attempting to authenticate with the rogue server, enabling offline password cracking.
- Increased Attack Surface: LLMNR adds another network protocol that needs to be secured and monitored. Disabling it reduces the attack surface, making it harder for attackers to exploit network communication.
- Network Noise: LLMNR can generate unnecessary network traffic, which can be exploited by attackers to map active devices and services on a network.
- mDNS protocol resolves hostnames to IP addresses within small networks that do not include a local name server. It is a zero-configuration service, using essentially the same programming interfaces, packet formats and operating semantics as unicast Domain Name System (DNS).
-
- Risks of mDNS being enabled: mDNS servers were not designed to be open to the Internet. When they are open to the Internet, they present two risks:
- They can expose the addresses of computers and devices inside your network to the attacker
- They can be used to amplify a DDOS attack on a victim’s server.
- Risks of mDNS being enabled: mDNS servers were not designed to be open to the Internet. When they are open to the Internet, they present two risks:
-
- NBNS (sometimes called WINS) stands for NetBIOS Name Service, which is a protocol for name resolution. NBNS performs the same function as LLMNR, but using UDP broadcast packets instead of multi cast packets. Browsers normally only attempt to use NBNS after attempts to use LLMNR have failed.
-
- Risks of NBNS being enabled:NetBIOS Name Service (NBNS) Spoofing: Attackers can spoof NetBIOS Name Service (NBNS) responses to redirect network traffic to malicious systems. This can lead to various attacks, such as Man-in-the-Middle (MITM) attacks and session hijacking
Potential impacts to watch out for:
- Disabling LLMNR and NBT-NS typically will not have any impact.
- If it does then you’ve got hosts relying on these protocols for name resolution!
- Disabling MDNS has an impact – mostly for service/device discovery.
- Workstations will not be able to find wireless screen mirroring devices (e.g. Miracast), Chromecasts, Printers and anything else that relies on MDNS.
- If this is a requirement remove the MDNS startup script from the GPO!
- Workstations will not be able to find wireless screen mirroring devices (e.g. Miracast), Chromecasts, Printers and anything else that relies on MDNS.
Technical Deployment:
Creating a GPO for this specific fix:
LLMNR
The individual Fix for LLMNR is the following:
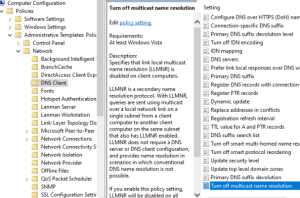
- Computer Configuration -> Policies -> Administrative Templates -> Network -> DNS Client -> Turn off multicast name resolution (Enable)
NBT-NS
- NETBIOS needs to be disabled on a per network interface basis and has no GPO setting. So we’ll need to use a startup script to do this.
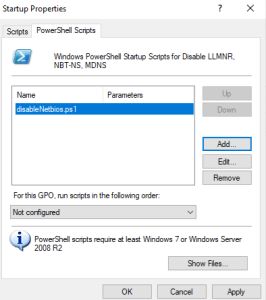
- Create disableNetbios.ps1 with the following contents.
wmic nicconfig where "TcpipNetbiosOptions=0 or TcpipNetbiosOptions=1" call SetTcpipNetbios 2or
PowerShell:
# Disable NetBios OverTCP/IP - {L1}
function Disable-NetBIOSoverTCP {
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey |foreach { Set-ItemProperty -Path "$regkey\$($_.pschildname)" -Name NetbiosOptions -Value 2 -Verbose}
Write-Host "For each interface found, NetBIOS over TCP/IP has been disabled" }
Disable-NetBIOSoverTCP
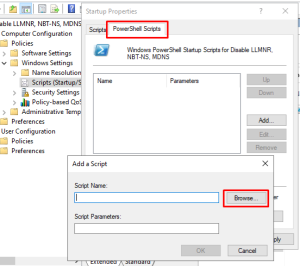
- Computer Configuration -> Policies -> Windows Settings -> Scripts -> Startup (Properties) -> PowerShell Scripts -> Add
-
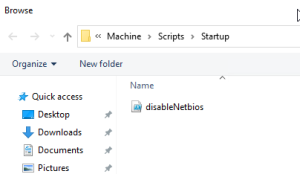
- Startup scripts need to be placed in locations that are accessible to clients. For most environments, you’ll probably be alright by placing it in the SYSVOL volume together with the GPO itself.
- Click the Browse button and paste the startup script into the location that explorer opens in and accept all the prompts.
-
MDNS
- Similar to NETBIOS, there’s no GPO setting to disable MDNS so we’ll be using a startup script once again to create a registry key.
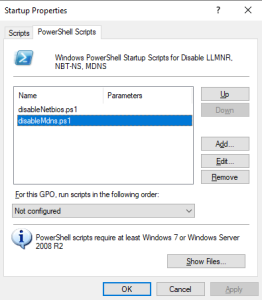
- Create disableMdns.ps1 with the following contents.
set-ItemProperty "HKLM:\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\" -Name EnableMDNS -Value 0 -Type DWord- Add the script as a startup script like we previously added the NETBIOS startup script.
-
References: