Active Directory Enumeration Detection technique for SIEM solutions:
I had an issue, I wanted to detect BloodHound. This was a favorite tool of mine when I did any Offensive team engagements in the past. This made issues though for when I transitioned more to the Defensive side. During IR, I could see this toolset hindsight, but it was pretty hard to detect proactively.
How do we figure out what BloodHound does under the hood? We reverse it. Digging into BH, I found that BH uses LDAPQueries to gather almost all of the data under the hood. This lead me to the question, I wonder what ADFind uses? Guess what? LDAPQueries. How about PowerView? Same thing. So, this means that we now found a shared similarity between multiple tool sets that threat actors, and Offensive Sec folks utilize to accomplish reconnaissance against domain users, computers, etc.
That all being said, I know there are known ways to detect these items out there such as monitoring all endpoints for “sharphound.exe” or “bloodhound.exe” or “Adfind.exe” etc. This is fine, and I do not discourage this alerting profile in environments, but they are limited and not complete. When I did Offensive Security engagements, never ever did I once run “sharphound.exe” in an environment. Would not happen. My workflow allowed me to easily run it under different name(s) tailored towards the environment I was attacking, and further I also ran it under brand spanking new hashes each time it was fired. So toss your Hashes, and name searches out the window. While these can catch the less sophisticated attacks, they will not get APTs (Advanced Persistent Threats).
So, that leads us to LDAPQuery monitoring right? Enable some sort of LDAP event logs, then monitor those usages, etc. You can do this, but what I learned from that process is, it can work sometimes. LDAPQuery monitoring is not complete. It is not all of the LDAP queries. Some are logged, some are not. So, depending on how good someone is with those toolsets, the attacks may go unnoticed. Try this for yourself, but let’s move on now to my method!
What if we tackle this a different way? What if we enable logging levels against either actual user accounts, or create canary/honey accounts that we leave disabled, and create event logs anytime something reads them, or that object’s properties. We can do this straight from the Domain Controller(s) only. Which means we no longer have the shortfalls of logging all endpoints, looking for a name, having holes in the LDAPQuery logs, having rogue assets on our network we do not have visibility into, etc.
Now we can detect when anything reads those account/computer/object properties. Fun fact about those tools, they literally go to AD and scream at the top of their lungs GIVE ME EVERYTHING YOU HAVE NOW! All properties are read. You can reduce this, which is why I ultimately suggest to create multiple of these and place them all over in different OUs, and anywhere in AD. Then if only one OU is hit, you are aware. If all are hit, you are insanely aware though.
Technical Steps:
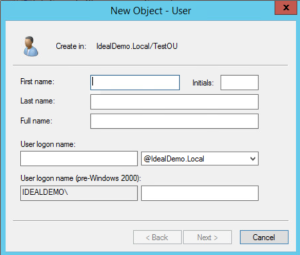
- Create a new object (user, computer, etc. may slightly vary) using ADUC (Active Directory Users and Computers)
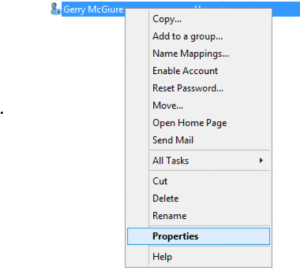
- I used Gerry McGuire for this test account. Choose something that looks real, Thanos, or Fake-anything is not good names here. You want threat actors or Red Team members to go after these accounts. After the account is created (if creating this for the detection purpose, leave the account disabled), Right-click the user in ADUC. Select “Properties” from the drop-down list:
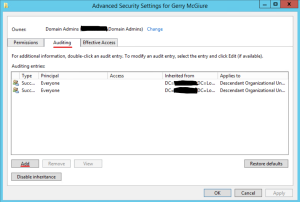
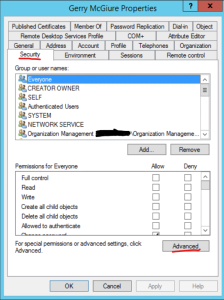
- Under Properties, you will want to now click on the Security tab at the top > Advanced at the bottom
- Add a new Principal “Everyone”
- From “Applies to” dropdown, choose “This object only”
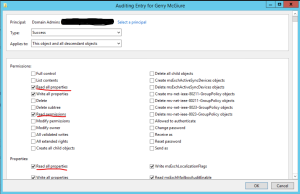
- Now we will need to select the Auditing tab > Add (Note here: you may have to change the ownership at the top to a group so that you can edit this auditing section).
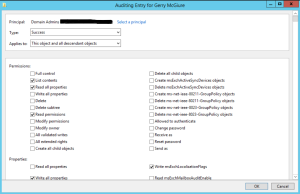
- Next, you may have to select a Principle (you can do a user or a group here) to be able to edit this next section. The original state looks like this:
-
- Uncheck all main permissions > Select only Read all properties, Read permissions.
- Click OK to save the changes.
- Now it is the time to test! Make sure that your Log source/SIEM solution is logging your Domain Controller(s) *yes all of them*. Further, run a test. Run Sharphound/Bloodhound in your environment from anywhere that can hit your DC. Did you get event ID 4662 event logs from your domain controllers. If you are, now we need to yank that event_code:4662 into a Graylog query.
SIEM / Graylog side:
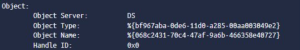
Next, if you have the logs in Graylog. You will need to grab the GUID of each user/computer/object and add those to Graylog in a Lookup Table. Then you will need to create some pipeline rules to make sure that you create a new field only when that information is in the log. Converting that GUID to the “Object Name” as a field in Graylog. You will take the following:
And now through the magic of Lookup Tables, and Pipeline rules, create something like this in Graylog:
This will allow you to know which object(s) were hit. This can give visibility into how tactful the threat actor is with these tools vs loud.
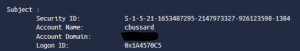
Now you created all of this, you have alerts flowing, what now!? Inside of the event log, there is a field (or should be a field) similar to the below couple:
The account name is the account that ran the tool that set this alert off. If/When you see that you note the time stamp(s) of this activity and you pivot over to the search and dig into event_code:4624 AND user_name:{insert username here} for a range of time surrounding when that alert went off. It will not tell you explicitly which toolset was used, but combining this with an EDR, or if you are logging that machine using a EDR, Sysmon, or SIEM agent, you should theoretically be able to dig into that deeper. If this is a rogue asset on the network, you have a high chance of reconnaissance happening. If you never expect to see that user, or the device tied back to that activity doing that activity, again you have a high likelihood of a compromise on the network.